BSM Services Reference
This chapter describes the important components of the BSM module, auditing and device allocation.
Auditing helps you detect potential security breaches by revealing suspicious or abnormal patterns of system usage. Auditing also provides a means to trace suspect actions back to a particular user, thus serving as a deterrent. If users know that their activities are likely to be audited, they might be less likely to attempt malicious activities.
This is a list of the reference information in this chapter.
Audit Commands
This section provides information about the commands that are used with the auditing service.
The Audit Daemon
The following list summarizes what the audit daemon, auditd, does.
auditd opens and closes audit log files in the directories that are specified in the audit_control file, in the order in which they are specified.
auditd reads audit data from the kernel and writes it to an audit log file.
auditd executes the audit_warn script when the audit directories fill past limits that are specified in the audit_control file. The script, by default, sends warnings to the audit_warn mail alias and to the console.
By default, when all audit directories are full, processes that generate audit records are suspended. In addition, the auditd command writes a message to the console and to the audit_warn mail alias. The audit policy can be reconfigured with the auditconfig. At this point, only the system administrator can log in to write audit files to tape, delete audit files from the system, or do other cleanup.
The auditd daemon can be started automatically when the machine is brought up to multiuser mode, or you can start it from the command line. When the audit daemon is started, it determines the amount of free space necessary for audit log files.
The daemon uses the list of audit directories in the audit_control file as possible locations for creating audit files. The audit daemon maintains a pointer into this list of directories, starting with the first directory. Every time the audit daemon needs to create an audit file, it puts the file into the first available directory in the list, starting at the audit daemon's current pointer. You can reset the pointer to the beginning of the list by running the audit -s command. When you use the audit -n command to instruct the daemon to switch to a new audit file, the new file is created in the same directory as the current file.
The audit Command
The audit command controls the actions of the audit daemon. The audit command can do the following tasks:
Enable and disable auditing
Reset the audit daemon
Adjust the auditing preselection mask on the local machine
Write audit records to a different audit log file
See the audit(1M) man page for a discussion of the available options.
The auditreduce Command
Use the auditreduce command to merge audit records from one or more input audit files or to perform a post selection of audit records. See the auditreduce(1M) man page. To merge the entire audit trail, you can run this command on the machine on which all the audit file systems for the installation are mounted.
The auditreduce command enables you to track all auditable actions on multiple machines from a single location. If you identically configure all machines at an installation for auditing, and create servers and local directories for the audit log files, then the auditreduce command can read the logical combination of all audit files in the installation as a single audit trail. auditreduce ignores how the records were generated or where they are stored. Without options, the auditreduce command merges audit records from all the audit files in all of the subdirectories in the audit root directory (/etc/security/audit) and sends the result to standard output. You can also place it into a single, chronologically ordered output file. The file contains binary data.
The auditreduce command also can select particular types of records for analysis. The merging and selecting functions of auditreduce are logically independent. auditreduce captures data from the input files as the records are read, before the files are merged and written to disk.
The praudit command makes the binary output of auditreduce readable.
By specifying options to the auditreduce command, you can also do the following:
Request audit records that were generated by only certain audit flags
Request audit records that were generated by one particular user
Request audit records that were generated on specific dates
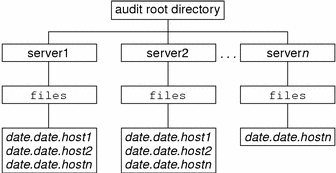
With no arguments, auditreduce checks the subdirectories within the /etc/security/audit directory, the default audit root directory. The command checks for a files directory in which the start-time.end-time.hostname files reside. The auditreduce command is very useful when the audit data for different hosts (Figure 25-1) or for different audit servers (Figure 25-2) reside in separate directories.
Figure 25-1 Audit Trail Storage Sorted by Host
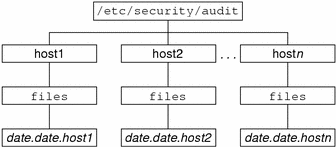
Figure 25-2 Audit Trail Storage Sorted by Server
When you do not store audit data in the default directory, perhaps because the partition for /etc/security/audit is very small, you can pass the auditreduce command another directory by using the -R option:
# auditreduce -R /var/audit-alt |
You can also specify a particular subdirectory by using the -S option:
# auditreduce -S /var/audit-alt/host1 |
You can direct auditreduce to process only certain audit log files by specifying them as command arguments:
# auditreduce /var/audit/egret/files/2001*.2001*egret |
For other options and additional examples, see the auditreduce(1M) man page.