PAM Components
The PAM software consists of a library, several modules, and a configuration file. New versions of several commands or daemons that take advantage of the PAM interfaces are also included.
The following figure below illustrates the relationship between the applications, the PAM library, the pam.conf file, and the PAM modules.
Figure 3-1 How PAM Works
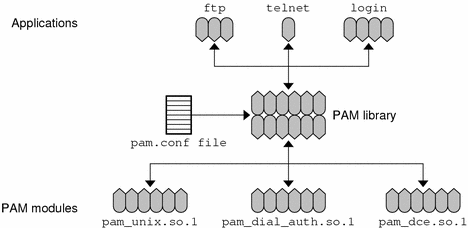
The applications (ftp, telnet, and login) use the PAM library to access the appropriate module. The pam.conf file defines which modules to use, and in what order they are to be used with each application. Responses from the modules are passed back through the library to the application.
The following sections describe the relationship between the PAM components and the applications.
PAM Library
The PAM library, /usr/lib/libpam, provides the framework to load the appropriate modules and manage the stacking process. The PAM library provides a generic structure to which all of the modules can plug in.
Stacking Feature
The PAM framework provides a method for authenticating users with multiple services by using stacking. Depending on the configuration, the user can be prompted for passwords for each authentication method. The order in which the authentication services are used is determined through the PAM configuration file.
Password-Mapping Feature
The stacking feature can require that a user remember several passwords. With the password-mapping feature, the primary password is used to decrypt the other passwords so that the user doesn't need to remember or enter multiple passwords. The other option is to synchronize the passwords across each authentication mechanism. Note that this strategy could increase the security risk, because the security of each mechanism is limited by the least secure password method that is used in the stack.
Changes to PAM for the Solaris 9 Release
The Solaris 9 release includes several enhancements to the PAM service. The following list highlights the most important changes:
To accommodate proper stacking, the pam_unix module is broken into single service modules. These modules provide the same capabilities as in the existing module. The capabilities are provided by the following modules: pam_authtok_get, pam_authtok_check, pam_authtok_store, pam_unix_auth, pam_dhkeys and pam_passwd_auth. See "PAM Modules" for information about the new modules.
New PAM services are included: cron, dtsession, ppp and ssh. See "Valid Service Names" for information about the new services.
The PAM configuration file was updated to include the new modules and services. See "Generic pam.conf File" for information about the configuration file.
PAM (Tasks)
This section discusses some tasks that might be required to make the PAM framework fully functional. In particular, you should be aware of some security issues that are associated with the PAM configuration file.
PAM (Task Map)
Task | Description | For Instructions |
|---|---|---|
Plan for your PAM Installation | Consider configuration issues and make decisions about them before you start the software configuration process. | "Planning for PAM" |
Add new PAM modules | Sometimes, site-specific modules must be written and installed to cover requirements that are not part of the generic software. This procedure covers the installation process. | "How to Add a PAM Module" |
Block access through ~/.rhosts | Steps to further increase security by preventing access through ~/.rhosts. | "How to Prevent Unauthorized Access From Remote Systems With PAM" |
Initiate error reporting | Steps to start the reporting of PAM error messages through syslog. | "How to Initiate PAM Error Reporting" |
Planning for PAM
When you are deciding how best to use PAM in your environment, start by focusing on these issues:
Determine what your needs are, especially which modules you should select.
Identify the services that need special attention. Use OTHER if appropriate.
Decide on the order in which the modules should be run.
Select the control flag for each module.
Choose any options that are necessary for each module.
Here are some suggestions to consider before you change the PAM configuration file:
Use the OTHER entry for each module type so that every application does not have to be included.
Make sure to consider the security implications of the sufficient and optional control flags.
Review the man pages that are associated with the modules to understand how each module functions, what options are available, and the interactions between stacked modules.
 Caution - If the PAM configuration file is misconfigured or becomes corrupted,
it is possible that even superuser would be unable to log in. Since the sulogin command does not use PAM, superuser would then be required
to boot the machine into single-user mode and fix the problem.
Caution - If the PAM configuration file is misconfigured or becomes corrupted,
it is possible that even superuser would be unable to log in. Since the sulogin command does not use PAM, superuser would then be required
to boot the machine into single-user mode and fix the problem. After you change the /etc/pam.conf file, review it as much as possible while you are still logged in as superuser. Test all the commands that might have been affected by your changes. For example, if you added a new module to the telnet service, use the telnet command and verify that the changes you made make the service behave as expected.
 How to Add a PAM Module
How to Add a PAM Module
Become superuser or assume an equivalent role.
Determine which control flags and other options should be used.
Refer to "PAM Modules" information on the modules.
Copy the new module to /usr/lib/security/sparcv9.
In the Solaris 8 release, the module should be copied to /usr/lib/security.
Set the permissions so that the module file is owned by root and that permissions are 555.
Edit the PAM configuration file, /etc/pam.conf, and add this module to the appropriate services.
Verification
It is very important to do some testing before the system is rebooted in case the configuration file is misconfigured. Run rlogin, su, and telnet before you reboot the system. If the service is a daemon that is spawned only once when the system is booted, it might be necessary to reboot the system before you can verify that the module has been added.
 How to Prevent Unauthorized Access From Remote Systems With PAM
How to Prevent Unauthorized Access From Remote Systems With PAM
Remove the rlogin auth rhosts_auth.so.1 entry from the PAM configuration file. This step prevents the reading of the ~/.rhosts files during an rlogin session and therefore prevents unauthenticated access to the local system from remote systems. All rlogin access requires a password, regardless of the presence or contents of any ~/.rhosts or /etc/hosts.equiv files.
Note - To prevent other unauthenticated access to the ~/.rhosts files, remember to disable the rsh service. The best way to disable a service is to remove the service entry from the /etc/inetd.conf file. Changing the PAM configuration file does not prevent the service from being started.
 How to Initiate PAM Error Reporting
How to Initiate PAM Error Reporting
Edit the /etc/syslog.conf file to add any of the following entries for PAM error reporting:
auth.alert - Messages about conditions that should be fixed immediately
auth.crit - Critical messages
auth.err - Error messages
auth.info - Informational messages
auth.debug - Debugging messages
Restart the syslog daemon, or send a SIGHUP signal to it to activate the PAM error reporting.